CloudBleed a Cloudflare flaw leaks customer data
“Cloudflare speeds up and protects millions of websites, APIs, SaaS services, and other properties connected to the Internet. Our Anycast technology enables our benefits to scale with every server we add to our growing footprint of data centers.”They provide these services for ~6 Million websites, and recently a researcher at google found a critical flaw in cloudflare’s inhouse parser that may have leaked passwords and authentication tokens. Tavis Ormandy a self-described “Vulnerability researcher at Google” currently working for Google’s Project Zero which is a security initiative found a bug on February 18th. He posted an issue on Feb 19th. he tweeted looking for anyone from cloudflare security to get in touch with him.
Cloudflare people got back to him right away and they worked on solving this issue ASAP. Unfortunately, the issue may be as old as September 2016. Cloudflare released a statement letting us know that the larger issue started on February 13th when a code update meant one in every 3,300,300 HTTP requests potentially resulted in memory leakage which doesn’t mean anything until you realize the massive amount of information being passed through the Cloudflare network. Tavis found when they “fetched a few live samples, and we observed encryption keys, cookies, passwords, chunks of POST data and even HTTPS requests for other major Cloudflare-hosted sites from other users”. there’s just so much information going through the Cloudflare network that we don’t know what has and hasn’t been affected until something is released showing an actual malicious leak. Unfortunately, a lot of data was cached by Google and other search engines and was available to be viewed as late as Feb 24th 2017. Cloudflare has been working with Google and Bing etc to remove such information before it can be maliciously used.Could someone from cloudflare security urgently contact me.
— Tavis Ormandy (@taviso) February 18, 2017
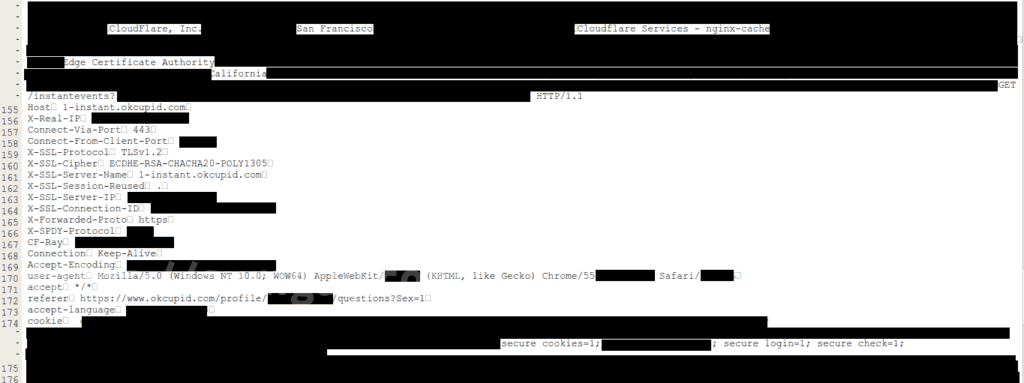 Ormandy’s original post :
Ormandy’s original post :On February 17th 2017, I was working on a corpus distillation project, when I encountered some data that didn’t match what I had been expecting. It’s not unusual to find garbage, corrupt data, mislabeled data or just crazy non-conforming data…but the format of the data this time was confusing enough that I spent some time trying to debug what had gone wrong, wondering if it was a bug in my code. In fact, the data was bizarre enough that some colleagues around the Project Zero office even got intrigued. It became clear after a while we were looking at chunks of uninitialized memory interspersed with valid data. The program that this uninitialized data was coming from just happened to have the data I wanted in memory at the time. That solved the mystery, but some of the nearby memory had strings and objects that really seemed like they could be from a reverse proxy operated by cloudflare – a major cdn service. A while later, we figured out how to reproduce the problem. It looked like that if an html page hosted behind cloudflare had a specific combination of unbalanced tags, the proxy would intersperse pages of uninitialized memory into the output (kinda like heartbleed, but cloudflare specific and worse for reasons I’ll explain later). My working theory was that this was related to their “ScrapeShield” feature which parses and obfuscates html – but because reverse proxies are shared between customers, it would affect *all* Cloudflare customers. We fetched a few live samples, and we observed encryption keys, cookies, passwords, chunks of POST data and even HTTPS requests for other major cloudflare-hosted sites from other users. Once we understood what we were seeing and the implications, we immediately stopped and contacted cloudflare security. This situation was unusual, PII was actively being downloaded by crawlers and users during normal usage, they just didn’t understand what they were seeing. Seconds mattered here, emails to support on a friday evening were not going to cut it. I don’t have any cloudflare contacts, so reached out for an urgent contact on twitter, and quickly reached the right people.
Cloudflare’s response to cloudbleed
Cloudflare has shown there is a good reason millions of sites trust them, they have stepped out in front and fixed the immediate issue within 6 hours of the report, and have been working on fixing the issue at large and hunting down any related bugs in the past few days.No 1Password data was put at risk through the bug reported earlier today. https://t.co/S7G62Qw85Q
— Cloudflare (@Cloudflare) February 24, 2017
Incident report on memory leak caused by Cloudflare parser bug – https://t.co/rTZ4bFw3uJ
— Cloudflare (@Cloudflare) February 23, 2017
Affected sites
Some of the companies affected have done their own due diligence and told users to change their passwords right away, while others like 1password & OkCupid have come to a different conclusion and informed their users but not forced a password change.Our investigation into the Cloudflare bug has revealed minimal exposure, if any. More details >> https://t.co/lYN7nq2oGq
— OkCupid (@okcupid) February 24, 2017
LastPass , a competitor to 1password, (I personally use LastPass but have no vested interest in the company) was not hosted behind Cloudflare and has had no impact from cloudbleed.Not to worry. Your secrets are still safe with me. 🤐 ❤️🔐 https://t.co/VSlHa967EG
— 1Password (@1Password) February 24, 2017
Download a list of all sites currently known to be using Cloudflare CDN/Proxy that may be affected by Cloudbleed by clicking this button below. https://sumguy.com/wp-content/uploads/2017/02/cloudflare_cloudbleed_20170223.zipIn response to recent news, LastPass does not use @cloudflare and is not affected by their recent security disclosure.
— LastPass Status (@LastPassStatus) February 24, 2017